Quantum key distribution leverages the principles of quantum mechanics to provide theoretically unbreakable encryption by detecting any eavesdropping on the key exchange, unlike classical key distribution methods which rely on computational assumptions and can be vulnerable to advances in computing power. Explore the rest of the article to understand how your data security can be enhanced through quantum technologies compared to traditional approaches.
Table of Comparison
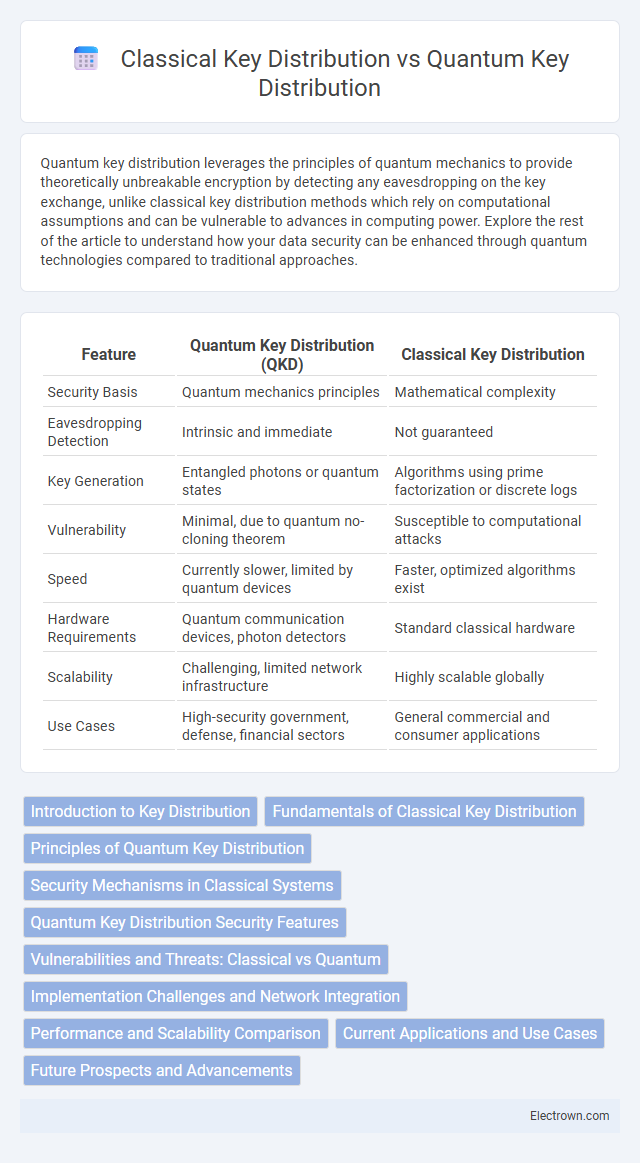
| Feature | Quantum Key Distribution (QKD) | Classical Key Distribution |
|---|---|---|
| Security Basis | Quantum mechanics principles | Mathematical complexity |
| Eavesdropping Detection | Intrinsic and immediate | Not guaranteed |
| Key Generation | Entangled photons or quantum states | Algorithms using prime factorization or discrete logs |
| Vulnerability | Minimal, due to quantum no-cloning theorem | Susceptible to computational attacks |
| Speed | Currently slower, limited by quantum devices | Faster, optimized algorithms exist |
| Hardware Requirements | Quantum communication devices, photon detectors | Standard classical hardware |
| Scalability | Challenging, limited network infrastructure | Highly scalable globally |
| Use Cases | High-security government, defense, financial sectors | General commercial and consumer applications |
Introduction to Key Distribution
Quantum key distribution (QKD) leverages principles of quantum mechanics to securely share encryption keys, ensuring any eavesdropping attempts are detectable through quantum state disturbances. Classical key distribution relies on computational complexity for security, making it vulnerable to advances in algorithmic attacks and quantum computing. Your data security benefits significantly from QKD's provable security model compared to traditional methods dependent on mathematical assumptions.
Fundamentals of Classical Key Distribution
Classical key distribution relies on mathematical algorithms and computational complexity to secure cryptographic keys, often using symmetric or asymmetric encryption methods such as RSA or Diffie-Hellman. This approach depends on the difficulty of solving problems like factoring large integers or discrete logarithms, which could be vulnerable to advances in computing power and algorithms. Your security can be compromised if attackers are able to break these mathematical assumptions, unlike quantum key distribution which uses quantum mechanics principles for potentially unbreakable encryption.
Principles of Quantum Key Distribution
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as superposition and entanglement, to enable secure communication by detecting eavesdropping through quantum states' disturbance. Unlike classical key distribution, which relies on mathematical complexity for security, QKD uses photon polarization or phase encoding to generate and share cryptographic keys with unconditional security guarantees grounded in the laws of physics. The BB84 and E91 protocols exemplify practical implementations, ensuring that any interception attempts alter the quantum bits, thus alerting the communicating parties.
Security Mechanisms in Classical Systems
Classical key distribution relies on mathematical algorithms such as RSA and Diffie-Hellman, which depend on the computational difficulty of factoring large numbers or solving discrete logarithms for security. These classical systems use symmetric or asymmetric cryptographic protocols combined with trusted third parties or public key infrastructures (PKIs) to facilitate secure key exchange. However, classical security mechanisms are vulnerable to advances in computational power and potential algorithmic breakthroughs, posing risks that quantum key distribution aims to mitigate.
Quantum Key Distribution Security Features
Quantum Key Distribution (QKD) leverages principles of quantum mechanics, such as photon polarization and quantum entanglement, to ensure unbreakable encryption keys by detecting any eavesdropping attempts instantly. Unlike classical key distribution methods, which rely on computational assumptions and can be vulnerable to attacks by powerful quantum computers, QKD offers unconditional security based on the laws of physics. Your secure communications benefit from QKD's ability to provide provably secure key exchange, ensuring long-term data confidentiality even against emerging cryptographic threats.
Vulnerabilities and Threats: Classical vs Quantum
Classical key distribution relies on complex mathematical algorithms that are vulnerable to computational attacks, including those from advanced quantum computers capable of breaking traditional encryption. Quantum key distribution (QKD) leverages the principles of quantum mechanics to detect eavesdropping, offering provably secure communication by using quantum states that collapse upon measurement. Your data security improves significantly with QKD as it mitigates risks associated with algorithmic weaknesses inherent in classical methods, preventing undetected interception or tampering.
Implementation Challenges and Network Integration
Quantum key distribution (QKD) faces significant implementation challenges such as the need for specialized hardware like single-photon detectors and maintaining quantum coherence over fiber optic or free-space channels. Network integration of QKD requires compatibility with existing classical communication infrastructure and protocols, often necessitating the development of hybrid quantum-classical networks to support key management and distribution. Classical key distribution methods benefit from mature, widely deployed systems that are easier to integrate but lack the unconditional security guarantees provided by QKD.
Performance and Scalability Comparison
Quantum key distribution (QKD) offers unparalleled security through quantum mechanics but faces limitations in performance and scalability due to distance constraints and the need for specialized hardware like single-photon detectors and quantum repeaters. Classical key distribution methods, such as RSA and Diffie-Hellman, provide higher throughput and easier integration with existing infrastructure but lack the provable security guarantees found in QKD. Scalability in QKD is currently limited to metropolitan areas or dedicated fiber links, whereas classical methods effectively scale across global networks with well-established protocols and hardware.
Current Applications and Use Cases
Quantum key distribution (QKD) is primarily utilized in high-security environments such as government communications, financial institutions, and critical infrastructure sectors where quantum-resistant encryption safeguards sensitive data against future quantum computer attacks. Classical key distribution remains widespread in everyday applications including internet transactions, VPNs, and wireless networks due to its established protocols like Diffie-Hellman and RSA, which offer practical security in current computational contexts. Emerging hybrid models integrate QKD with classical systems to enhance security in telecommunications and cloud services, providing a quantum-safe layer for data transmission without compromising compatibility.
Future Prospects and Advancements
Quantum key distribution (QKD) promises unprecedented security by leveraging quantum mechanics to detect eavesdropping, a significant advancement over classical key distribution relying on computational hardness. Future prospects include integration with emerging quantum networks and satellite-based QKD systems, enabling global secure communication. Your data protection will benefit from continuous improvements in QKD protocols, increased transmission rates, and enhanced error correction methods, positioning quantum technologies as the cornerstone of next-generation cybersecurity.
quantum key distribution vs classical key distribution Infographic
 electrown.com
electrown.com