Quantum key distribution leverages the principles of quantum mechanics to enable secure communication by detecting any eavesdropping attempts, ensuring your encryption keys remain confidential. Explore the rest of the article to understand how this compares to traditional public key distribution methods and which might best suit your security needs.
Table of Comparison
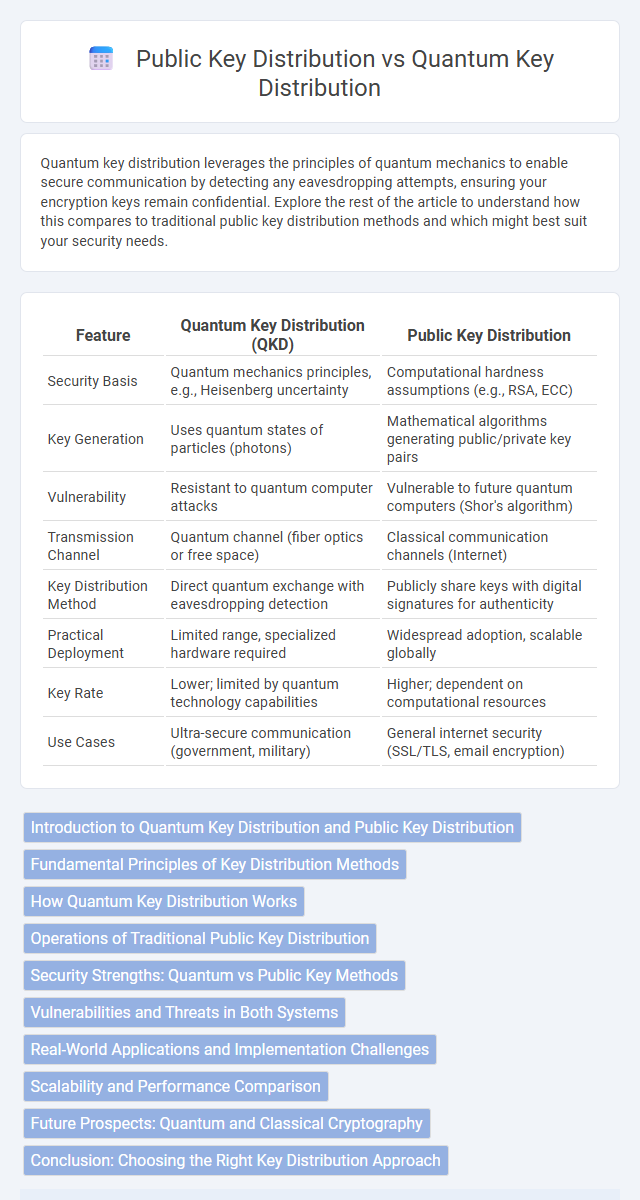
| Feature | Quantum Key Distribution (QKD) | Public Key Distribution |
|---|---|---|
| Security Basis | Quantum mechanics principles, e.g., Heisenberg uncertainty | Computational hardness assumptions (e.g., RSA, ECC) |
| Key Generation | Uses quantum states of particles (photons) | Mathematical algorithms generating public/private key pairs |
| Vulnerability | Resistant to quantum computer attacks | Vulnerable to future quantum computers (Shor's algorithm) |
| Transmission Channel | Quantum channel (fiber optics or free space) | Classical communication channels (Internet) |
| Key Distribution Method | Direct quantum exchange with eavesdropping detection | Publicly share keys with digital signatures for authenticity |
| Practical Deployment | Limited range, specialized hardware required | Widespread adoption, scalable globally |
| Key Rate | Lower; limited by quantum technology capabilities | Higher; dependent on computational resources |
| Use Cases | Ultra-secure communication (government, military) | General internet security (SSL/TLS, email encryption) |
Introduction to Quantum Key Distribution and Public Key Distribution
Quantum Key Distribution (QKD) uses principles of quantum mechanics to securely share cryptographic keys, enabling unconditionally secure communication by detecting any eavesdropping attempts due to quantum state disturbances. Public Key Distribution relies on mathematical algorithms and computational hardness assumptions, such as RSA or ECC, to exchange encryption keys over insecure channels but is vulnerable to advances in quantum computing. QKD offers future-proof security through quantum protocols like BB84, while public key methods remain widespread but risk obsolescence as quantum technology progresses.
Fundamental Principles of Key Distribution Methods
Quantum key distribution (QKD) relies on the principles of quantum mechanics, such as superposition and entanglement, to securely generate and share cryptographic keys, ensuring any eavesdropping attempt alters the quantum state and is detected. Public key distribution uses mathematical algorithms based on computational hardness assumptions, like RSA or ECC, to encrypt keys exchanged over insecure channels, depending on problems like integer factorization or discrete logarithms for security. While QKD offers unconditional security rooted in physical laws, public key distribution's security is conditional on the difficulty of solving specific mathematical problems.
How Quantum Key Distribution Works
Quantum Key Distribution (QKD) uses the principles of quantum mechanics to securely share encryption keys by transmitting quantum bits, or qubits, through a communication channel. These qubits, often encoded in the polarization states of photons, allow two parties to detect eavesdropping due to the disturbance caused by measurement on quantum states. This process ensures an unconditionally secure key exchange, contrasting with Public Key Distribution, which relies on computational hardness assumptions vulnerable to advances in algorithms or quantum computing.
Operations of Traditional Public Key Distribution
Traditional public key distribution relies on asymmetric cryptography, where a pair of mathematically linked keys--a public key and a private key--enable secure communication without prior secret exchange. Public keys are distributed openly through digital certificates and trusted Certificate Authorities (CAs), ensuring authenticity and preventing man-in-the-middle attacks. Encryption and signature verification use these keys to maintain confidentiality and data integrity, but the system's security depends on computational hardness assumptions vulnerable to advances in quantum computing.
Security Strengths: Quantum vs Public Key Methods
Quantum key distribution (QKD) offers unparalleled security strengths by leveraging the principles of quantum mechanics, ensuring that any eavesdropping attempt on the key exchange can be detected immediately. Public key distribution relies on mathematical complexity, such as RSA or ECC algorithms, making it vulnerable to advances in quantum computing and algorithmic breakthroughs. Your security strategy significantly benefits from QKD when long-term confidentiality and protection against future computational threats are critical.
Vulnerabilities and Threats in Both Systems
Quantum key distribution (QKD) provides secure communication by leveraging the principles of quantum mechanics, minimizing vulnerabilities such as interception and eavesdropping that plague classical public key distribution systems. Public key distribution is susceptible to computational attacks like factoring large integers or solving discrete logarithms, which quantum computers threaten to break efficiently. Your data security benefits from QKD's inherent protection against such threats, but practical implementation challenges and potential side-channel attacks remain concerns in both approaches.
Real-World Applications and Implementation Challenges
Quantum key distribution (QKD) offers unparalleled security for sensitive communications by leveraging quantum mechanics, making it ideal for government and financial sectors requiring secure key exchange resistant to future quantum computer attacks. Public key distribution, widely implemented in internet protocols like HTTPS and email encryption, faces challenges from increasing computational power and potential quantum threats, necessitating upgrades to post-quantum cryptography. You must consider that QKD implementation faces practical barriers such as high costs, limited distance range due to quantum signal attenuation, and infrastructure requirements, whereas public key systems benefit from established networks and ease of integration.
Scalability and Performance Comparison
Quantum key distribution (QKD) offers unparalleled security through quantum mechanics but faces scalability challenges due to the need for specialized hardware and limited transmission distances, impacting performance in large networks. Public key distribution relies on well-established algorithms like RSA and ECC, providing easy scalability and high-speed key exchange over existing infrastructure, yet it remains vulnerable to future quantum attacks. Performance in QKD systems is currently constrained by key generation rates and distance limitations, while classical public key systems excel in widespread deployment and speed but lack quantum resistance.
Future Prospects: Quantum and Classical Cryptography
Quantum key distribution (QKD) offers unparalleled security by leveraging the principles of quantum mechanics to detect eavesdropping, ensuring that your cryptographic keys remain absolutely secure. Classical public key distribution relies on mathematical complexity, which faces increasing risks from future quantum computers potentially breaking current encryption algorithms. Integrating QKD with classical cryptographic methods represents a promising approach for future-proofing secure communications against both present and emerging threats.
Conclusion: Choosing the Right Key Distribution Approach
Quantum key distribution offers unparalleled security through the principles of quantum mechanics, making it highly resistant to eavesdropping and future quantum computing threats. Public key distribution relies on computational hardness assumptions, which could be compromised by advances in algorithms or quantum computing. Selecting the right key distribution method depends on the required security level, infrastructure capabilities, and long-term data protection needs, with quantum key distribution favored for ultra-secure communications and public key systems for widespread, practical deployment.
quantum key distribution vs public key distribution Infographic
 electrown.com
electrown.com