Quantum cryptography leverages principles of quantum mechanics, such as quantum entanglement and superposition, to provide theoretically unbreakable encryption, unlike classical cryptography which relies on complex mathematical algorithms vulnerable to advances in computational power. Explore the rest of the article to understand how these technologies differ and what implications they hold for your data security.
Table of Comparison
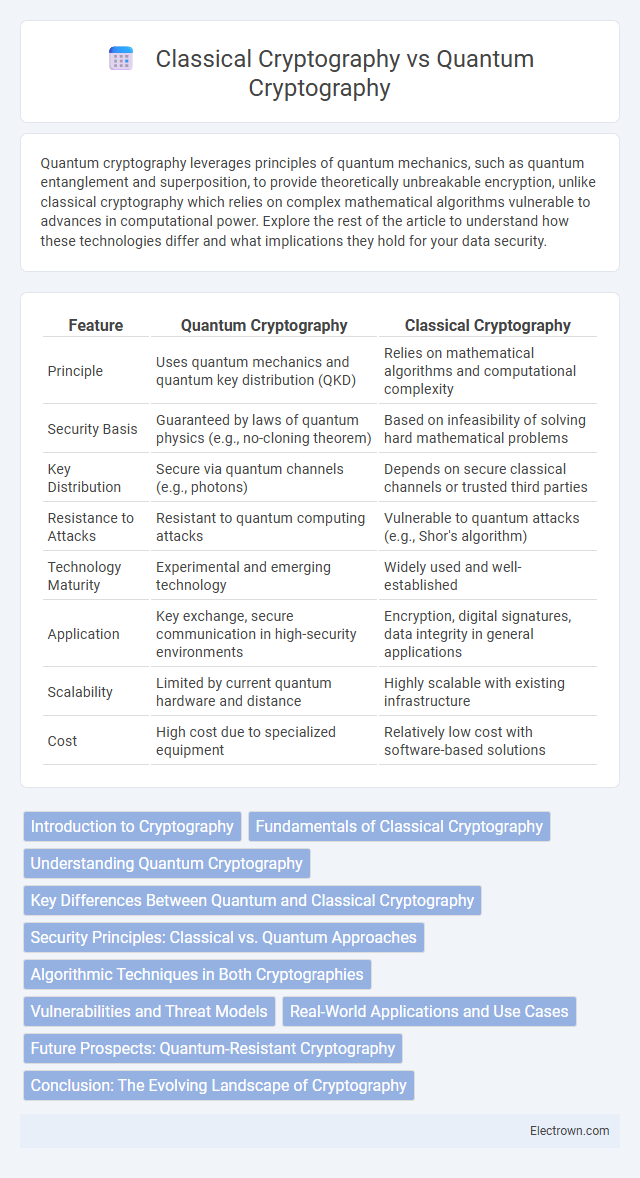
| Feature | Quantum Cryptography | Classical Cryptography |
|---|---|---|
| Principle | Uses quantum mechanics and quantum key distribution (QKD) | Relies on mathematical algorithms and computational complexity |
| Security Basis | Guaranteed by laws of quantum physics (e.g., no-cloning theorem) | Based on infeasibility of solving hard mathematical problems |
| Key Distribution | Secure via quantum channels (e.g., photons) | Depends on secure classical channels or trusted third parties |
| Resistance to Attacks | Resistant to quantum computing attacks | Vulnerable to quantum attacks (e.g., Shor's algorithm) |
| Technology Maturity | Experimental and emerging technology | Widely used and well-established |
| Application | Key exchange, secure communication in high-security environments | Encryption, digital signatures, data integrity in general applications |
| Scalability | Limited by current quantum hardware and distance | Highly scalable with existing infrastructure |
| Cost | High cost due to specialized equipment | Relatively low cost with software-based solutions |
Introduction to Cryptography
Cryptography secures communication by encoding information, with classical cryptography relying on mathematical algorithms such as RSA and AES to protect data. Quantum cryptography leverages principles of quantum mechanics, specifically quantum key distribution (QKD) protocols like BB84, to ensure theoretically unbreakable encryption. Unlike classical methods vulnerable to increasing computational power, quantum cryptography offers security based on the laws of physics, making it resistant to future quantum computer attacks.
Fundamentals of Classical Cryptography
Classical cryptography relies on mathematical algorithms and computational hardness assumptions, such as factoring large prime numbers or discrete logarithms, to secure data through symmetric or asymmetric encryption methods. It primarily employs key-based techniques like AES for symmetric encryption and RSA for public-key encryption, ensuring confidentiality, integrity, and authentication in digital communication. Despite its widespread use, classical cryptography faces potential vulnerabilities against advances in computing power, particularly the emergence of quantum computers capable of efficiently solving problems underpinning its security.
Understanding Quantum Cryptography
Quantum cryptography leverages the principles of quantum mechanics, such as superposition and entanglement, to create secure communication channels resistant to eavesdropping. Unlike classical cryptography, which relies on computational hardness assumptions like factoring large numbers, quantum cryptography offers unconditional security through protocols like Quantum Key Distribution (QKD). Understanding quantum cryptography can enhance Your data protection strategy by ensuring encryption keys are generated and shared with provable security against future quantum computer attacks.
Key Differences Between Quantum and Classical Cryptography
Quantum cryptography leverages principles of quantum mechanics, such as superposition and entanglement, to enable secure key distribution through quantum key distribution (QKD), which is theoretically immune to eavesdropping. Classical cryptography relies on complex mathematical algorithms, like RSA or AES, whose security depends on computational difficulty, making them vulnerable to future quantum computers. Your data security can be significantly enhanced with quantum cryptography's ability to detect interception attempts instantly, unlike classical methods that rely solely on computational hardness.
Security Principles: Classical vs. Quantum Approaches
Classical cryptography relies on computational hardness assumptions, such as factoring large primes, to secure data, which can be vulnerable to advances in algorithmic efficiency and computing power. Quantum cryptography employs principles like quantum key distribution (QKD), utilizing quantum mechanics properties such as superposition and entanglement to guarantee theoretically unbreakable security based on the laws of physics. Your communication security is significantly enhanced with quantum approaches, as any eavesdropping attempt alters quantum states, making intrusion detectable in real-time.
Algorithmic Techniques in Both Cryptographies
Quantum cryptography utilizes principles like quantum key distribution (QKD) based on quantum mechanics, ensuring unconditional security through algorithms such as BB84 and E91 that detect eavesdropping by measuring quantum states. Classical cryptography relies on complex mathematical problems, employing algorithms like RSA and AES that depend on computational hardness assumptions for security. Your choice between these approaches depends on the required security level and the feasibility of implementing quantum-resistant protocols in communication systems.
Vulnerabilities and Threat Models
Quantum cryptography leverages quantum mechanics principles to provide theoretically unbreakable encryption, effectively mitigating vulnerabilities inherent in classical cryptography such as susceptibility to brute-force attacks and computational limitations. Classical cryptography relies on mathematical complexity, making it vulnerable to emerging threats like quantum computing, which can potentially break widely used algorithms including RSA and ECC. Your security strategy must consider that while quantum cryptography resists many known threat models, practical implementation challenges and side-channel attacks still pose risks requiring robust countermeasures.
Real-World Applications and Use Cases
Quantum cryptography offers unbreakable encryption through quantum key distribution (QKD), which secures sensitive communications in sectors like finance, government, and healthcare against potential future quantum computer attacks. Classical cryptography remains widely used for everyday applications such as online banking, email security, and digital signatures due to its established protocols and ease of implementation. Your choice between the two should consider the required security level and the existing infrastructure compatibility for real-world deployment.
Future Prospects: Quantum-Resistant Cryptography
Quantum-resistant cryptography, also known as post-quantum cryptography, is designed to secure data against attacks from quantum computers that exploit Shor's algorithm to break classical encryption methods such as RSA and ECC. Researchers are actively developing lattice-based, hash-based, and code-based cryptographic algorithms to replace vulnerable classical algorithms while ensuring performance and scalability. The National Institute of Standards and Technology (NIST) is in the process of standardizing these quantum-resistant algorithms to bolster cybersecurity in the era of quantum computing.
Conclusion: The Evolving Landscape of Cryptography
Quantum cryptography leverages principles of quantum mechanics to provide theoretically unbreakable security, contrasting with classical cryptography that relies on computational complexity for encryption strength. Advancements in quantum computing threaten to compromise many classical cryptographic algorithms, prompting accelerated research into quantum-resistant methods. The evolving landscape of cryptography is marked by a critical shift towards integrating quantum-safe protocols to safeguard information in the era of quantum technology.
quantum cryptography vs classical cryptography Infographic
 electrown.com
electrown.com