Quantum resistance uses quantum mechanical principles to secure data against attacks from quantum computers, while classical resistance relies on traditional cryptographic methods vulnerable to such advanced threats. Explore the rest of the article to understand how these approaches impact your data security in the evolving digital landscape.
Table of Comparison
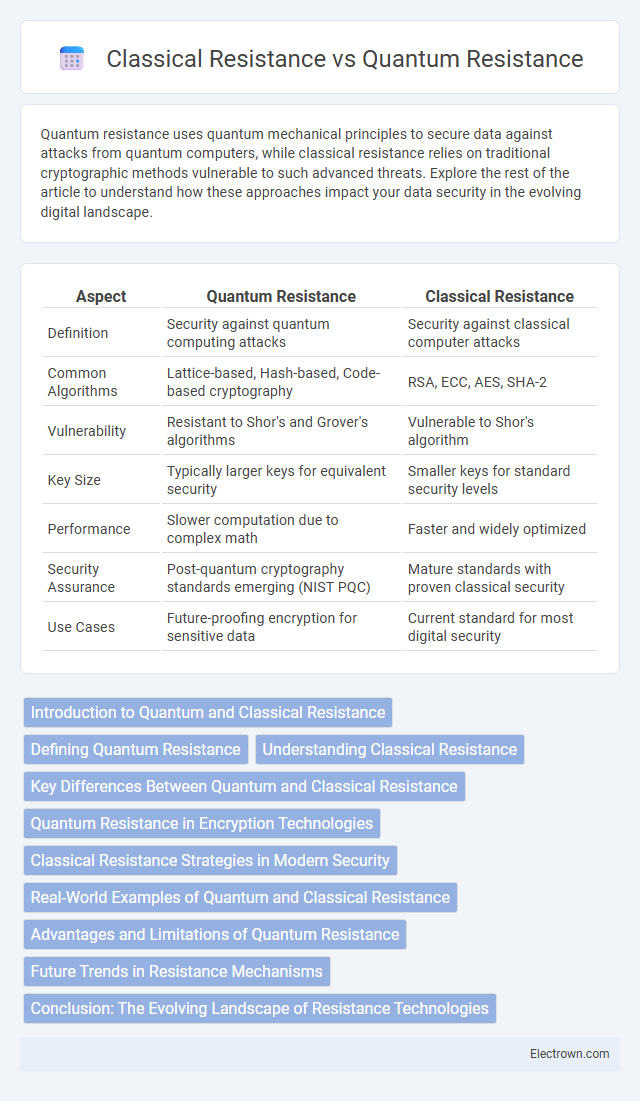
| Aspect | Quantum Resistance | Classical Resistance |
|---|---|---|
| Definition | Security against quantum computing attacks | Security against classical computer attacks |
| Common Algorithms | Lattice-based, Hash-based, Code-based cryptography | RSA, ECC, AES, SHA-2 |
| Vulnerability | Resistant to Shor's and Grover's algorithms | Vulnerable to Shor's algorithm |
| Key Size | Typically larger keys for equivalent security | Smaller keys for standard security levels |
| Performance | Slower computation due to complex math | Faster and widely optimized |
| Security Assurance | Post-quantum cryptography standards emerging (NIST PQC) | Mature standards with proven classical security |
| Use Cases | Future-proofing encryption for sensitive data | Current standard for most digital security |
Introduction to Quantum and Classical Resistance
Quantum resistance refers to the ability of cryptographic systems to withstand attacks by quantum computers, which leverage quantum algorithms like Shor's algorithm to break traditional encryption methods. Classical resistance involves protecting data against attacks by classical computers using well-established cryptographic techniques such as RSA and ECC, which are vulnerable to quantum decryption. Understanding the differences between quantum and classical resistance is crucial for developing secure protocols that safeguard your digital information in the emerging era of quantum computing.
Defining Quantum Resistance
Quantum resistance refers to the ability of cryptographic algorithms to withstand attacks from quantum computers, which leverage quantum bits to solve complex problems far more efficiently than classical computers. Classical resistance, on the other hand, pertains to security measures that protect against traditional computational attacks using classical algorithms and hardware. Your cybersecurity strategy should prioritize quantum-resistant algorithms to ensure protection as quantum computing capabilities advance.
Understanding Classical Resistance
Classical resistance in electrical circuits is defined by the opposition to the flow of electric current, primarily caused by collisions between free electrons and atoms within conductive materials. This resistance is quantitatively described by Ohm's Law, where resistance (R) equals voltage (V) divided by current (I), and is influenced by material properties such as resistivity, temperature, and cross-sectional area. Understanding classical resistance is essential for designing circuits and predicting energy loss due to heat dissipation in traditional electronic devices.
Key Differences Between Quantum and Classical Resistance
Quantum resistance relies on principles of quantum mechanics, such as superposition and entanglement, enabling resistance mechanisms that can adapt at the atomic or subatomic level. Classical resistance, governed by Ohm's law, depends on electron flow obstruction within conductive materials, influenced by factors like temperature and material impurities. Quantum resistance often exhibits non-linear characteristics and can manipulate electron wavefunctions, while classical resistance is typically linear and predictable under standard conditions.
Quantum Resistance in Encryption Technologies
Quantum resistance in encryption technologies ensures data security against attacks from quantum computers by using algorithms such as lattice-based, hash-based, and code-based cryptography that remain secure under quantum computational models. Classical resistance relies on traditional cryptographic methods like RSA and ECC, which quantum algorithms like Shor's algorithm can easily break, making them vulnerable to future quantum attacks. Developing and implementing quantum-resistant encryption is critical for maintaining confidentiality and integrity in digital communications as quantum computing advances.
Classical Resistance Strategies in Modern Security
Classical resistance strategies in modern security primarily rely on mathematical problems such as factoring large integers and discrete logarithms, foundational to RSA and ECC encryption algorithms. These methods use computational hardness assumptions that classical computers struggle to solve efficiently, providing robust protection against conventional cyber threats. However, advancements in quantum computing pose significant risks to these strategies, as quantum algorithms like Shor's algorithm can potentially break these cryptosystems exponentially faster than classical methods.
Real-World Examples of Quantum and Classical Resistance
Quantum resistance is exemplified by lattice-based cryptography methods used in securing sensitive government communications, ensuring protection against quantum computer attacks. Classical resistance is demonstrated by RSA encryption, widely used in online banking and e-commerce, offering robust security against conventional computational threats. Your secure data benefits from understanding these differences in quantum and classical resistance applications.
Advantages and Limitations of Quantum Resistance
Quantum resistance offers enhanced security against quantum computing attacks by utilizing algorithms such as lattice-based cryptography and hash-based signatures, which are designed to withstand quantum decryption methods. These algorithms provide robust protection for sensitive data and secure communication channels, especially in post-quantum scenarios where classical encryption systems like RSA and ECC become vulnerable. However, quantum-resistant algorithms often face limitations including increased computational requirements, larger key sizes, and integration challenges with existing classical infrastructure, potentially impacting performance and scalability.
Future Trends in Resistance Mechanisms
Quantum resistance mechanisms leverage principles of quantum computing and quantum cryptography to protect data against attacks from quantum algorithms like Shor's, which can break classical encryption standards such as RSA and ECC. Future trends emphasize the development of post-quantum cryptographic algorithms standardized by institutions like NIST, ensuring resilience against both classical and quantum computational threats. Emerging approaches include lattice-based, hash-based, code-based, and multivariate polynomial-based cryptographic schemes designed to maintain robust security in the evolving threat landscape.
Conclusion: The Evolving Landscape of Resistance Technologies
Quantum resistance technologies harness lattice-based cryptography and hash-based signatures to counteract the threats posed by quantum computing's superior processing power. Classical resistance relies primarily on traditional algorithms such as RSA and ECC, which are vulnerable to quantum attacks like Shor's algorithm. As quantum computing advances, integrating post-quantum cryptographic solutions becomes essential for maintaining long-term data security and protecting sensitive information in digital communications.
Quantum Resistance vs Classical Resistance Infographic
 electrown.com
electrown.com